Introduction
Managing user and device access in large organisations—especially in schools or Multi Academy Trusts (MATs)—can be complex when roles, departments, or devices change frequently. Traditionally, IT teams manually update group memberships, a process that is both time-consuming and prone to error. Every time a teacher moves to a new department, a student changes year group, or a new laptop is deployed, someone has to update permissions manually.
Dynamic groups in Microsoft Entra ID solve this challenge by automatically adding or removing users and devices based on attributes such as job title, department, year group, device type, or enrolment profile. This automation ensures that access is always accurate and up to date, reducing administrative overhead and improving security.
Creating Dynamic User Groups in Microsoft Entra
Step 1: Sign in to Microsoft Entra Admin Center
- Go to https://entra.microsoft.com
- Sign in with your Global Administrator or Groups Administrator account.
Step 2: Navigate to Groups
- In the left-hand menu, click Groups.
- Select All groups.
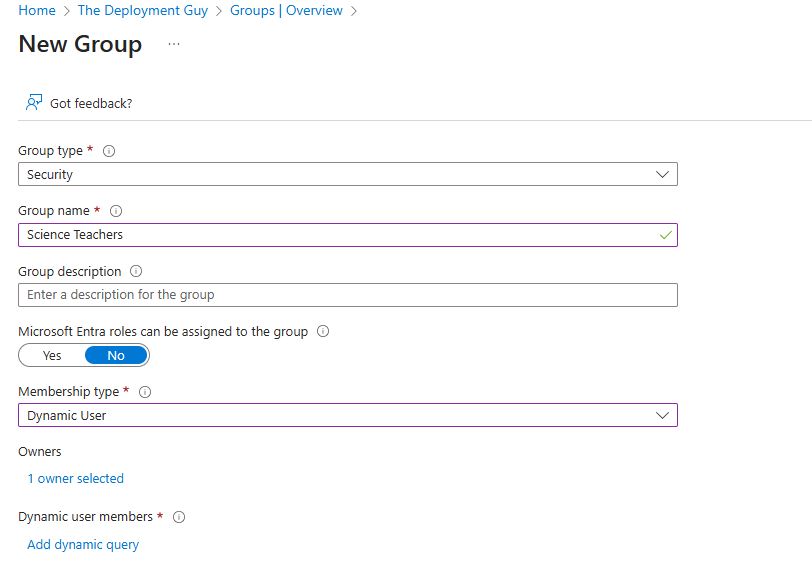
Step 3: Create a New Group
- Click + New group.
- Choose:
- Group type: Security or Microsoft 365.
- Membership type: Dynamic User or Dynamic Device.
- Enter a name and description for the group.
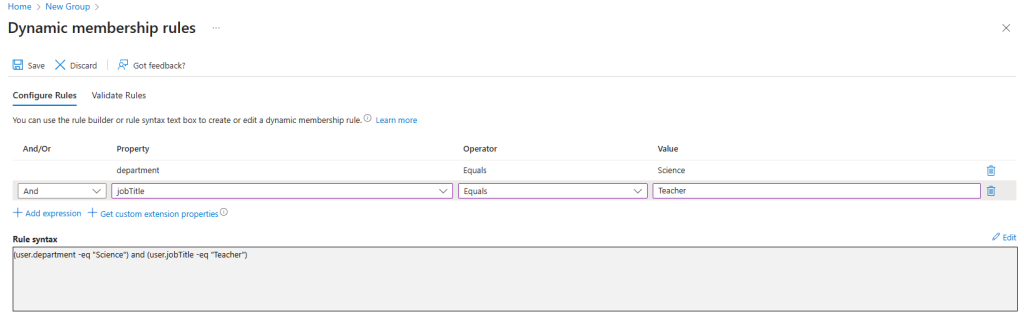
Step 4: Add Dynamic Membership Rules
- Under Membership type, click Add dynamic query.
- Select Rule Builder for a no-code experience.
- Use dropdown menus to define conditions:
- Example: department equals “Science”.
- Add more conditions using AND/OR logic (e.g., jobTitle starts with “Teacher”).
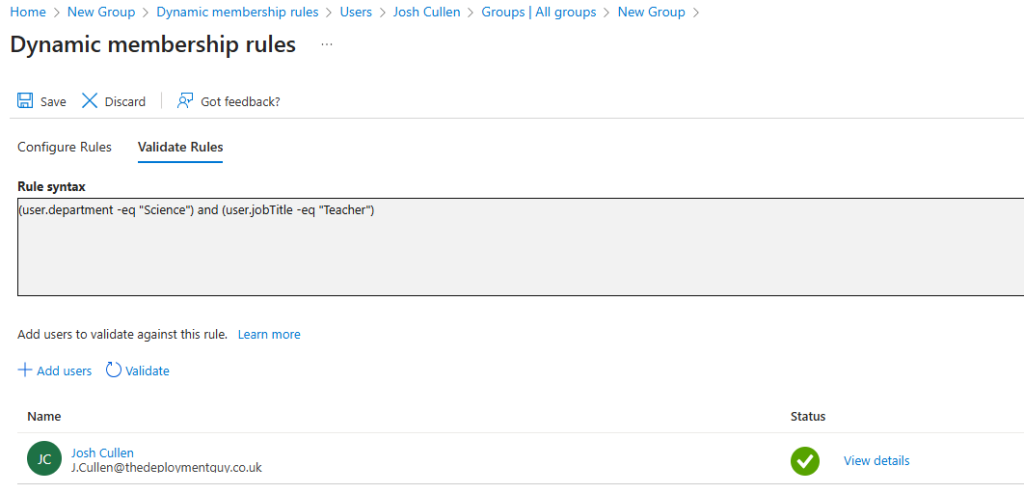
Step 5: Validate and Save
- Click Validate Rules to ensure your conditions work.
- Preview the expression.
- Click Save.
- Membership updates will occur automatically based on your rules.
Creating Dynamic User Groups in Microsoft Entra
1. Combine Multiple Conditions with AND/OR
Scenario: Add users who are in the Admin department and have the job title starting with “Manager”.
(user.department -eq "Admin") -and (user.jobTitle -startsWith "Manager")
2. Include Multiple Departments
Scenario: Add users from either Science or Maths.
(user.department -eq "Science") -or (user.department -eq "Maths")3. Nested Logic for Complex Scenarios
Scenario: Add users in Maths OR Science, but only if they are located in Burnley.
((user.department -eq "Maths") -or (user.department -eq "Science")) -and (user.city -eq "Burnley")4. Match Email Domain
Scenario: In a school or Multi Academy Trust (MAT), it’s common to manage users across multiple sites, each with its own email domain. For example, staff at different campuses or departments may use distinct email suffixes.
If you want to create a dynamic group that includes users whose email addresses end with @TheDeploymentGuy.co.uk, you can use the following rule:
(user.mail -endsWith "@TheDeploymentGuy.co.uk"6. Use Wildcards for Job Titles
Scenario: In a school or Multi Academy Trust (MAT), staff may have job titles that share a common keyword but differ slightly—for example, “IT Technician”, “Science Technician”, or “Design Technician”.
If you use the -eq (equals) operator in a dynamic group rule, the value must match exactly. This means only users with the precise job title "IT Technician" would be included.
To capture all technician roles, you can use the -contains operator instead:
(user.jobTitle -contains "Technician")Creating Dynamic Device Groups in Microsoft Entra
Dynamic device groups allow IT teams in schools or Multi Academy Trusts (MATs) to automatically group devices based on attributes like ownership, operating system, enrolment profile, and compliance status. These groups are essential for applying policies, deploying apps, and managing updates efficiently.
1. Group All Windows Devices
Scenario: In a school or Multi Academy Trust (MAT), you may want to target all devices running Windows for updates or app deployment.
(device.operatingSystem -eq "Windows")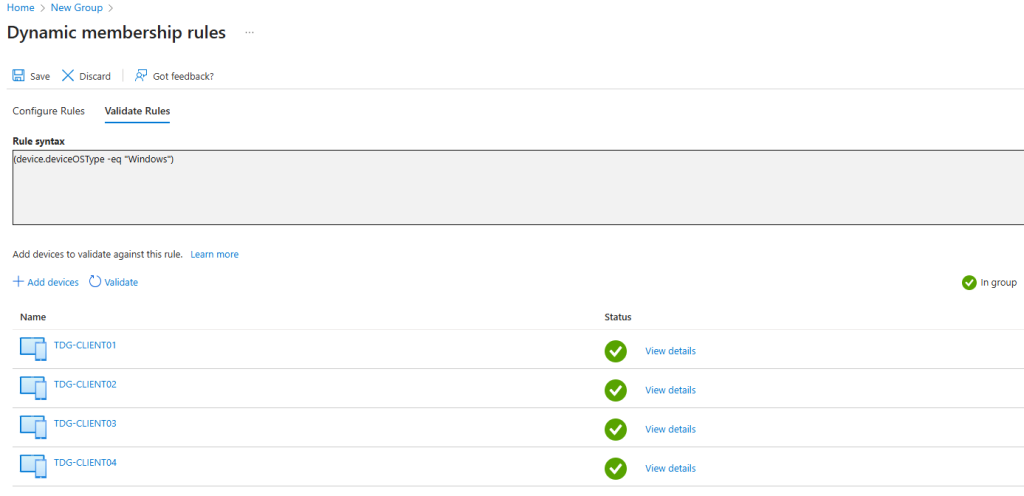
2. Group All Organisation-Owned Devices
Scenario: You may need to separate school-owned devices from personal ones for applying security policies or compliance settings.
(device.deviceOwnership -eq "Company")3. Group Devices Enrolled via a Specific Enrollment Profile
Scenario: If your school uses multiple enrolment profiles for different kinds of devices (e.g., for staff vs students iPads), you can target devices by an enrollment profile name.
(device.enrollmentProfileName -eq "iPadOS - Student iPad Enrollment Profile")4. Group All Company-Owned macOS Devices
Scenario: In a school or Multi Academy Trust (MAT), you may want to target all organisation-owned Mac devices for applying security baselines or deploying macOS-specific apps.
(device.deviceOSType -eq "MacOS") -and (device.deviceOwnership -eq "Company")5. Apply Policies to Devices Based on OS Version
Scenario: You may want to identify and manage Windows devices that have not yet been updated to the latest Windows 11 feature update (25H2). This is useful for phased rollouts, security compliance, or targeted upgrade campaigns.
(device.deviceOSType -eq "Windows") and (device.deviceOSVersion -ne "10.0.26200")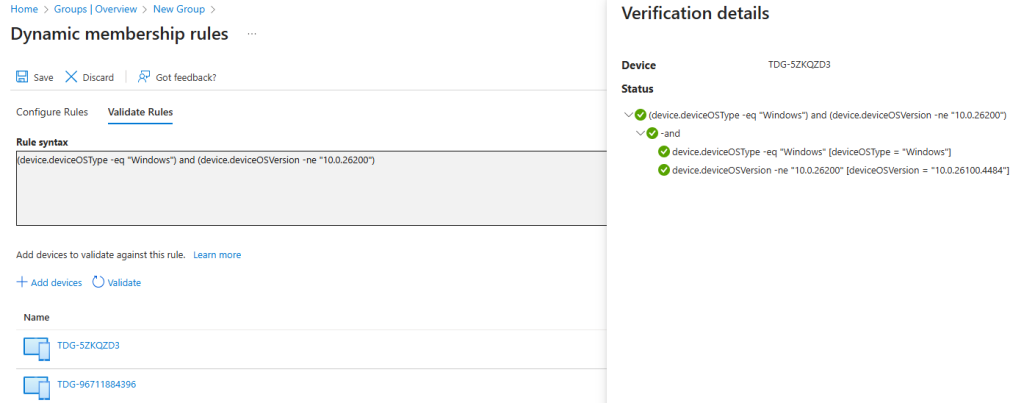
6. Group All Windows Autopilot Devices
Scenario: For advanced targeting, combine multiple attributes including compliance state.
(device.devicePhysicalIDs -any (_ -startsWith "[ZTDId]"))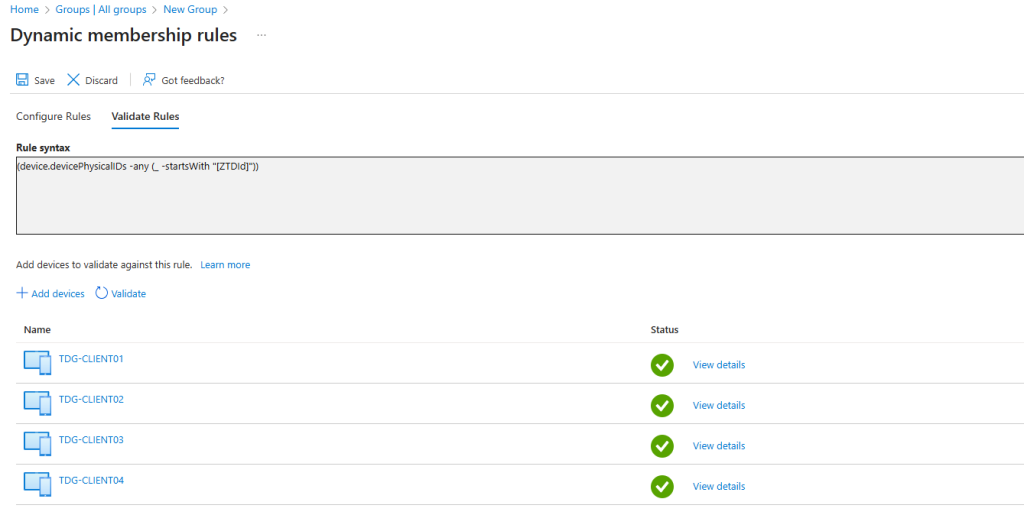
Pro Tips for Dynamic Groups
1. Validate Before You Commit
Use Validate Rules in the Microsoft Entra admin centre to preview which users or devices will be included before saving the rule. This helps avoid accidental over-inclusion or exclusion.
2. Switch Between Rule Builder and Syntax View
Start with the Rule Builder for simple conditions, then switch to Syntax View for advanced logic like -any or multiple conditions
3. Understand Licensing Requirements
Dynamic groups require Microsoft Entra ID P1 (or higher) or Intune for Education for each unique user in any dynamic group.
4. Keep Rules Efficient
Avoid overly complex or inefficient operators like -match unless necessary. Use -eq, -in, or -startsWith for better performance and faster processing.
5. Plan for Processing Delays
Large tenants or complex rules can take hours to process. If you’re making bulk changes, expect delays and avoid frequent edits to the same rule.
6. Combine with Group-Based Licensing
Dynamic groups work perfectly with group-based licensing. Assign licences to the group, and they’ll automatically flow to members as they join or leave.
Final Thoughts
Dynamic groups in Microsoft Entra ID are more than a convenience they’re a foundation for secure, scalable, and efficient IT management. By automating user and device group membership, you eliminate repetitive manual tasks, reduce human error, and ensure that access policies remain accurate as people change roles or devices are replaced.
Whether it’s automatically assigning licences to new staff, applying security baselines to school owned devices, or targeting Autopilot deployments, dynamic groups keep your environment organised and compliant. Combined with group-based licensing and Intune policies, they enable a truly hands-off approach to provisioning and lifecycle management freeing IT teams to focus on strategic improvements rather than routine admin.
For more detailed guidance, visit https://learn.microsoft.com/en-us/entra/identity/users/manage-dynamic-group
📺 Enjoyed this article? Let’s stay connected!
If you enjoyed this article and want to dive deeper into the topics I cover, head over to my YouTube channel where I share practical tips, walkthroughs, and insights tailored for tech enthusiasts and support professionals.
👉 Click here to visit the channel (YouTube) and don’t forget to subscribe so you never miss an update. Your support helps the channel grow and keeps the content coming!


